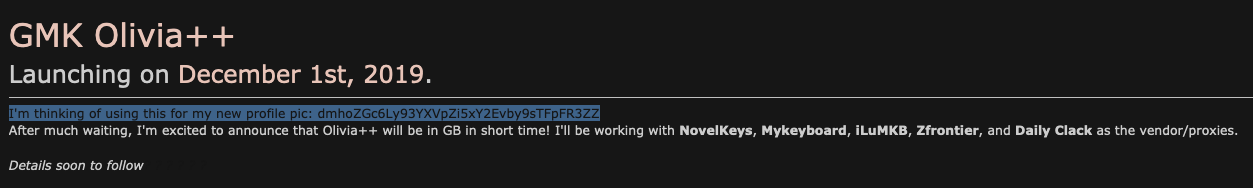
The game is afoot
Olivia posted the Olivia++ IC on Geehack with the text in the screenshot set to black. I happened to be using the Tapatalk app on my phone and it doesn’t care about text color properties and so it was immediately visible.
The important bit is this string
dmhoZGc6Ly93YXVpZi5xY2Evby9sTFpFR3ZZ
If you run that string through a Base64 decoder you get: vhhdg://wauif.qca/o/lLZEGvY
Immediately this is recognizable as a URL but it’s clearly encrypted. It appears to be fairly simple but I wasn’t familiar with the pattern so I started trying to line up what I could clearly make out like so:
vhhdg://wauif.qca/o/lLZEGvY
https://_ _ _ _ _.com/
abcdefghijklmnopqrstuvwxyz
m op st c h
You can see the pattern pretty quickly here and I later found out it’s called ROT12 or “Rotate by 12 places”
Once solved, we get the decrypted URL:
https://imgur.com/a/xXLQShK
This Imgur album has a single image with another Base64 string caption V2UgbXVzdCBnbyBkZWVwZXIuLi4= that decodes to “We must go deeper…”
The image itself is this PNG
Here’s where things get more interesting…
Steganography
That’s a term I hadn’t heard before but after googling phrases like “hidden message in image” I came across it and a number of tools available that can help extract information. One of those tools is Zsteg. I saw it in passing on a list of commonly used tools for Steganography but it wasn’t until user lemongrassii mentioned using it that I figured it was worth a shot.
After installing Zsteg, you can run it on an image with the -a flag to check all known methods of steganography. It’s run like so:
$ zsteg -a image.png
This gives us something interesting:
b2,rgb,lsb,yx .. zlib: data="IyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMj\r\nIyMjIyMjIyMjIyMjIyMjIy...", offset=59, size=1505
breaking this down
b2,rgb,lsb,yx means 2 bits across the R, G, and B channels, where the least significant BIT comes first and in the yx order.
the concept behind LSB or least significant bit steganography is that you can change the last few bits of pixel data without corrupting the image and this allows for data to be hidden within images without much integrity loss.
In this case, the last two bits are used across all of the color channels.
The next thing we see is zlib: data="IyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMj\r\nIyMjIyMjIyMjIyMjIyMjIy...". This looked promising and on further investigation zlib is a compression library. I stumbled upon this tool CyberChef when searching for ways to extract the data which will come in handy in a moment.
The last bit of important information is: offset=59 which tells us how far this data is offset from the start of the file.
Next we run the following:
$ zsteg image.png -E b2,rgb,lsb,yx -l 0 > olivia
This extracts the data based on the steganography pattern specified and puts it into a file. So far it’s unusable because it hasn’t been inflated with Zlib yet.
I took the file and loaded it into CyberChef which very handily has an option to inflate data using Zlib and to specify an offset which we know is 59.
After doing this we get the string:
IyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMj
IyMjIyMjIyMjIyMjIyMjIyMKIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMj
IyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMKIyMjIyMjIyMjIyMjIyMjIyMjIyMj
IyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMKIyMj
IyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMj
IyMjIyMjIyMjIyMjIyMKIyMjIyMjIyMgICAgICAgICAgICAgICMjICAgICAgICAjIyAgICAgICMj
IyMgICMjICAjIyAgICAgICAgICAgICAgIyMjIyMjIyMKIyMjIyMjIyMgICMjIyMjIyMjIyMgICMj
IyMjIyMjICAgICAgICAgICMjICAjIyAgIyMjIyAgIyMjIyMjIyMjIyAgIyMjIyMjIyMKIyMjIyMj
IyMgICMjICAgICAgIyMgICMjIyMgICMjICAjIyAgICAjIyMjIyMgICMjICAjIyAgIyMgICAgICAj
IyAgIyMjIyMjIyMKIyMjIyMjIyMgICMjICAgICAgIyMgICMjIyMjIyAgICAjIyMjICAgICAgICAj
IyAgICAjIyAgIyMgICAgICAjIyAgIyMjIyMjIyMKIyMjIyMjIyMgICMjICAgICAgIyMgICMjIyMj
IyAgICAgICAgIyMgICMjICAgICAgIyMjIyAgIyMgICAgICAjIyAgIyMjIyMjIyMKIyMjIyMjIyMg
ICMjIyMjIyMjIyMgICMjIyMgICMjICAjIyAgICAjIyAgIyMgICMjIyMjIyAgIyMjIyMjIyMjIyAg
IyMjIyMjIyMKIyMjIyMjIyMgICAgICAgICAgICAgICMjICAjIyAgIyMgICMjICAjIyAgIyMgICMj
ICAjIyAgICAgICAgICAgICAgIyMjIyMjIyMKIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjICAgICMj
IyMgICMjICAjIyAgIyMjIyAgIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMKIyMjIyMjIyMgICAg
IyMgICAgIyMgICMjIyMgICMjIyMgICAgICAgICAgICAjIyAgICAjIyAgIyMjIyMjIyMjIyAgIyMj
IyMjIyMKIyMjIyMjIyMjIyMjICAgICAgIyMjIyAgIyMjIyAgIyMjIyMjICAgICAgICAgICAgIyMg
ICMjICAgICMjICAgICMjIyMjIyMjIyMKIyMjIyMjIyMjIyMjIyMgICMjIyMgICMjICAgICMjIyMg
ICMjICAgICMjIyMjIyMjICAjIyMjICAjIyMjICAjIyMjIyMjIyMjIyMKIyMjIyMjIyMgICMjICAj
IyMjICAjIyAgICAjIyMjIyMjIyMjICAjIyAgICAjIyAgICAjIyAgIyMjIyAgIyMjIyAgIyMjIyMj
IyMKIyMjIyMjIyMgICAgICAgICAgIyMgICAgIyMgICAgIyMjIyAgICAgICAgIyMjIyMjICAjIyAg
ICAjIyMjIyMjIyAgIyMjIyMjIyMKIyMjIyMjIyMjIyAgICAjIyMjICAjIyMjIyMgICAgIyMgICMj
IyMjIyAgICAgICMjIyMjIyAgICAgICAgICAgICAgIyMjIyMjIyMKIyMjIyMjIyMgICMjICAjIyAg
ICAgICAgIyMgICAgIyMjIyMjICAgICAgIyMjIyAgICAgICMjICAgICMjICAjIyAgIyMjIyMjIyMK
IyMjIyMjIyMgICAgICAjIyAgIyMjIyMjIyMjIyMjIyMgICAgICAjIyMjIyMjIyAgIyMgICAgICAg
ICMjICAjIyAgIyMjIyMjIyMKIyMjIyMjIyMjIyMjIyMjIyMjIyMgICAgIyMgICMjICAgICMjIyMj
IyMjIyMgICMjIyMjIyMjIyMjIyAgIyMjIyMjIyMjIyMjIyMKIyMjIyMjIyMgICAgIyMjIyAgICAj
IyMjICAjIyAgICAjIyMjIyMjIyAgIyMgICAgICAjIyMjIyMgICMjICAgICMjIyMjIyMjIyMKIyMj
IyMjIyMgICAgICAgICMjIyMgICMjICAgICMjIyMgICAgICAgICMjIyMjIyAgIyMjIyMjIyMjIyAg
IyMjIyAgIyMjIyMjIyMKIyMjIyMjIyMgICAgIyMgICMjICAjIyAgICAjIyAgICAjIyAgIyMjIyAg
IyMjIyMjIyMjIyAgICAjIyAgICAjIyMjIyMjIyMjIyMKIyMjIyMjIyMgICAgIyMgICMjIyMgICAg
IyMjIyMjICAjIyAgIyMjIyMjICAgICMjICAgICAgICAgICAgICAgICMjIyMjIyMjIyMKIyMjIyMj
IyMjIyMjIyMjIyMjIyMjIyMjICAjIyMjIyMgICAgIyMjIyAgICAjIyMjICAjIyMjIyMgICAgIyMj
IyMjIyMjIyMjIyMKIyMjIyMjIyMgICAgICAgICAgICAgICMjIyMgICMjICAjIyAgIyMgICMjIyMj
IyAgICAjIyAgIyMgICAgIyMjIyMjIyMjIyMjIyMKIyMjIyMjIyMgICMjIyMjIyMjIyMgICMjIyMj
IyAgICAgICAgIyMjIyAgICAjIyAgICAjIyMjIyMgICMjIyMjIyMjIyMjIyMjIyMKIyMjIyMjIyMg
ICMjICAgICAgIyMgICMjICAgICAgICAgICAgIyMgICMjIyMjIyAgICAgICAgICAgICAgIyMjIyMj
IyMjIyMjIyMKIyMjIyMjIyMgICMjICAgICAgIyMgICMjICAjIyAgIyMjIyAgICAjIyMjIyMgICAg
ICAgICMjIyMjIyMjIyMgICMjIyMjIyMjIyMKIyMjIyMjIyMgICMjICAgICAgIyMgICMjIyMgICAg
ICAgICAgIyMgICMjICAgICMjIyMgICMjICAgICMjICAgICAgIyMjIyMjIyMKIyMjIyMjIyMgICMj
IyMjIyMjIyMgICMjICAgICMjICAjIyMjIyMjIyMjIyMjIyMjIyMgICAgICAjIyAgICAjIyAgIyMj
IyMjIyMKIyMjIyMjIyMgICAgICAgICAgICAgICMjICAgICMjIyMjIyMjICAjIyAgIyMgICAgICAj
IyAgICAgICMjIyMjIyMjIyMjIyMjIyMKIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMj
IyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMKIyMjIyMjIyMjIyMjIyMj
IyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMj
IyMKIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMj
IyMjIyMjIyMjIyMjIyMjIyMjIyMKIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMj
IyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMjIyMK
Once again I ran the string through a Base64 decoder to get:
##########################################################################
##########################################################################
##########################################################################
##########################################################################
######## ## ## #### ## ## ########
######## ########## ######## ## ## #### ########## ########
######## ## ## #### ## ## ###### ## ## ## ## ########
######## ## ## ###### #### ## ## ## ## ########
######## ## ## ###### ## ## #### ## ## ########
######## ########## #### ## ## ## ## ###### ########## ########
######## ## ## ## ## ## ## ## ## ########
######################## #### ## ## #### ##########################
######## ## ## #### #### ## ## ########## ########
############ #### #### ###### ## ## ## ##########
############## #### ## #### ## ######## #### #### ############
######## ## #### ## ########## ## ## ## #### #### ########
######## ## ## #### ###### ## ######## ########
########## #### ###### ## ###### ###### ########
######## ## ## ## ###### #### ## ## ## ########
######## ## ############## ######## ## ## ## ########
#################### ## ## ########## ############ ##############
######## #### #### ## ######## ## ###### ## ##########
######## #### ## #### ###### ########## #### ########
######## ## ## ## ## ## #### ########## ## ############
######## ## #### ###### ## ###### ## ##########
######################## ###### #### #### ###### ##############
######## #### ## ## ## ###### ## ## ##############
######## ########## ###### #### ## ###### ################
######## ## ## ## ## ###### ##############
######## ## ## ## ## #### ###### ########## ##########
######## ## ## #### ## ## #### ## ## ########
######## ########## ## ## ################## ## ## ########
######## ## ######## ## ## ## ################
##########################################################################
##########################################################################
##########################################################################
##########################################################################
It looked kind of like ASCII art from the output I saw in the web browser so I brought it into VS Code which was pretty lucky because I have the mini-map open which gives you a zoomed out view of your code and I was able to make out a QR code.
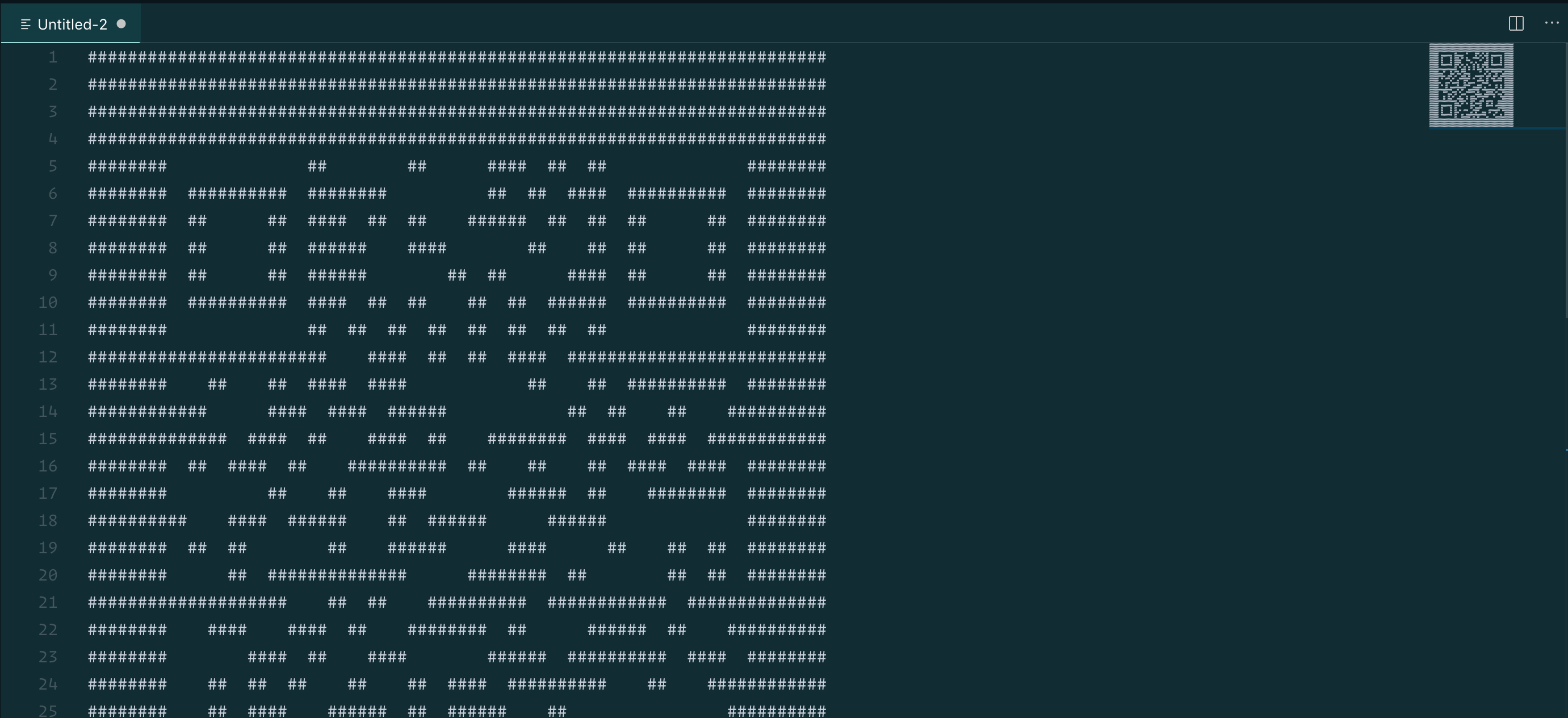
I scanned the QR code which took me here:
Countdown Clock and thus solving the mystery.
Mystery solved
I’ve never done one of these scavenger hunts despite hearing about similar concepts before. I guess it was the fact that it was tied to a keyboard related thing that I was interested.
I wasn’t prepared for how much I learned through this process that I’ll probably never use again but it sure was fun!
Thanks @olivia for creating such a fun interest check and I look forward to the next challenge!